From Playbooks to Protocols: Why Determinism is Dying
For 10 years, we optimized for Idempotency. Now, we are deploying Agents that are Probabilistic. How do we survive?
Posted on January 15, 2025 by Cabin crew team
For 10 years, we optimized for Idempotency. Now, we are deploying Agents that are Probabilistic. How do we survive?
Posted on January 15, 2025 by Cabin crew team

For 10 years, we optimized for Idempotency (running Ansible twice gets the same result). Now, we are deploying Agents that are Probabilistic (running them twice gets different results). How do we survive?
The evolution of infrastructure automation tells a story of increasing abstraction and decreasing human intervention:
The dark ages. Every deployment was a snowflake. Scripts were brittle, imperative, and impossible to audit. If a script failed halfway through, you had no idea what state your system was in.
The golden age of Determinism. We moved from imperative (“do this”) to declarative (“ensure this state exists”). The same playbook, run twice, produces the same infrastructure. This was revolutionary.
Key innovation: Idempotency. If a task has already been completed, running it again does nothing. This made automation safe, predictable, and auditable.
The next evolution: Desired State. You declare what you want, and the control plane continuously reconciles reality with your intent. This introduced the concept of “eventual consistency” but maintained determinism—the same YAML always produces the same cluster state.
Enter 2024. We are now deploying AI Agents into production pipelines. These agents:
The problem? They are probabilistic. Run the same agent twice with the same input, and you get different outputs. This is not a bug—it’s a feature. LLMs are creative, adaptive, and non-deterministic by design.
This creates a new form of drift: Intelligence Drift.
Configuration Drift was when your servers slowly diverged from the declared state (someone SSH’d in and manually edited a config file).
Intelligence Drift is when your AI Agent decides that the “best” solution to a database performance issue is to drop the indexes. Or when it hallucinates a dependency that doesn’t exist. Or when it refactors your authentication logic and introduces a security vulnerability.
The tools of the last decade cannot govern this.
In the Ansible era, we could review the playbook before running it. The playbook was static. It didn’t change between review and execution.
With AI Agents, the code is generated at runtime. By the time you review the PR, the agent has already:
You cannot “review” this in a meaningful way. The cognitive load is too high. The speed is too fast.
At Cabin Crew, we believe the solution is not to slow down AI—it’s to add governance layers that operate at AI speed.
We adapted the Terraform Plan/Apply model for AI workflows:
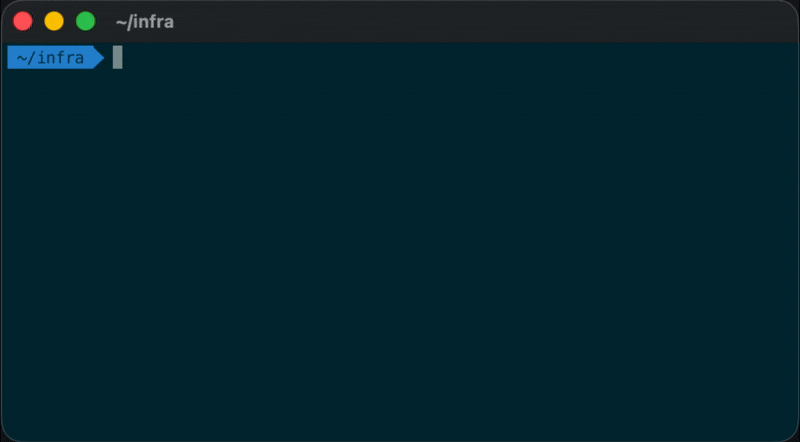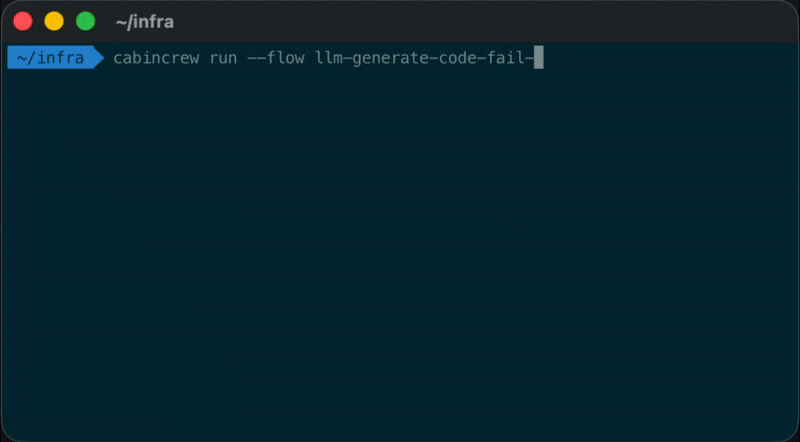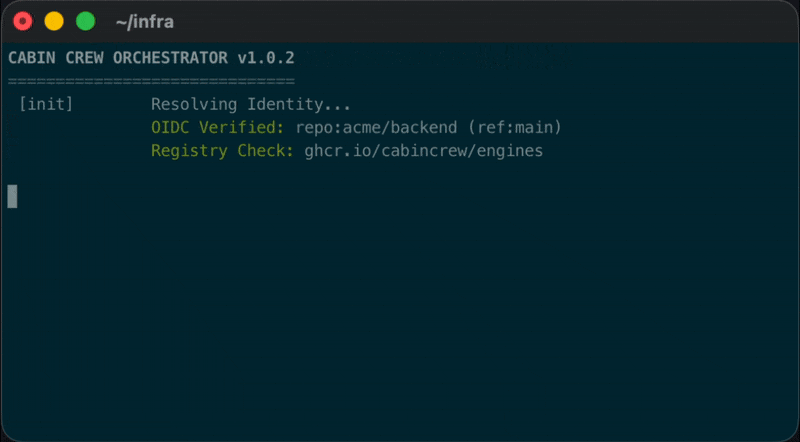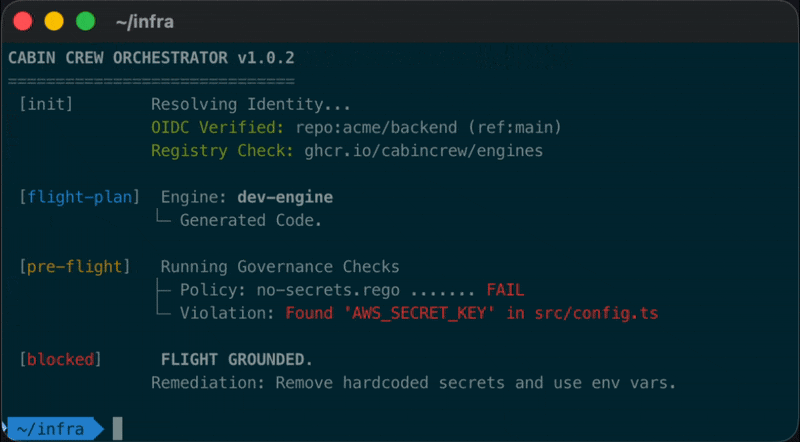
The AI Agent runs in read-only mode. It generates artifacts (code diffs, Terraform plans, database migrations) but executes no side effects. This is the “Flight Plan”—a declaration of intent.
The Orchestrator pauses execution. It feeds the generated artifacts into a Policy Engine (OPA). Policies validate:
If the policy fails, the workflow halts. No exceptions.
Only if approved, the Agent re-runs in write mode. It receives a sealed “State Token” from the planning phase to ensure it executes the exact plan that was approved.
The Ansible generation built systems where humans were in the loop—you wrote the playbook, reviewed it, and clicked “run.”
The AI generation requires humans to be on the loop—you define the policies, the AI executes within those boundaries, and you audit the results.
This is not about replacing DevOps engineers. It’s about elevating them from script writers to policy architects.
If you’re running Ansible in production today, you’re already thinking about governance. You have:
The question is: Can your governance scale to 1000x the velocity?
AI Agents will generate more code in a day than your team writes in a month. Your current review process will become the bottleneck.
The answer is not to hire more reviewers. The answer is to codify your governance.
At Cabin Crew, we’re building the Universal Chain of Custody for Autonomous Workflows. We treat AI Agents like pilots:
This is the next evolution of control. From playbooks to protocols.
The era of Governed Intelligence has begun.
Interested in learning more? Check out the Cabin Crew Protocol or explore our platform components.